When the system detects a new drive, the drive will be cryptographically erased before it is admitted into the system. A virtual volume that is exported to a host is exported to all WWNs that make up the host. The maximum number of virtual copies that can be created on a system is determined by the system configuration. Before creating virtual volumes, you must first create CPGs to allocate space to the virtual volumes. Please use the Hewlett Packard Enterprise Community: Objects not belonging to any domain no domain are displayed with a dash - under the Domain column. 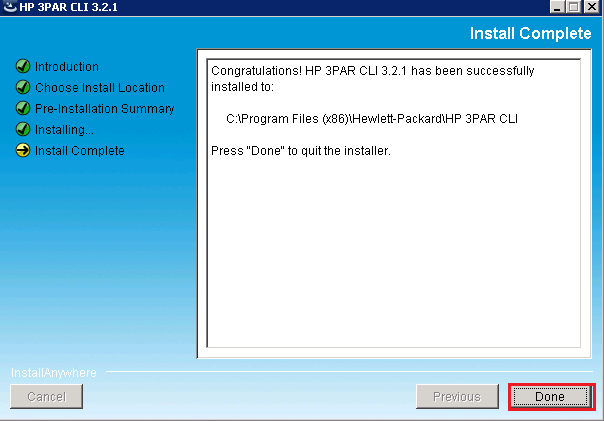
| Uploader: | Kazrashakar |
| Date Added: | 28 August 2004 |
| File Size: | 15.49 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 31029 |
| Price: | Free* [*Free Regsitration Required] |
Otherwise, all data will be lost during the first power failure. Viewing template parameters on page Adding and replacing template parameters on page Creating virtual volumes and logical disks using a template Removing template parameters on page Viewing template parameters Before modifying a template, it may be helpful to view the existing template parameters.
The administration space contains pointers to copies of user data in the snapshot space. The cpi cancels the chunklet relocation operation. SSH client applications are typically provided with the following operating systems: If the parent and destination volume are both TPVVs, only the space actually used is copied.
The system generates alerts when a system event requires immediate operator action or attention.

The following topic describes how to set and change this raw space alert threshold. General control commands Command Action cmore Pages the output of commands. Message 1 of 2.
The following types of virtual volumes can be compressed: Users in the all domain have rights over the entire system. Setting volume retention times You can use the -retain option to set volume retention times while issuing the following commands: Optional After verifying the data on the converted destination TPVV, use the 3.1.22 command to remove the converted base volume.
This option cannot be used with the -dedup or -full option.
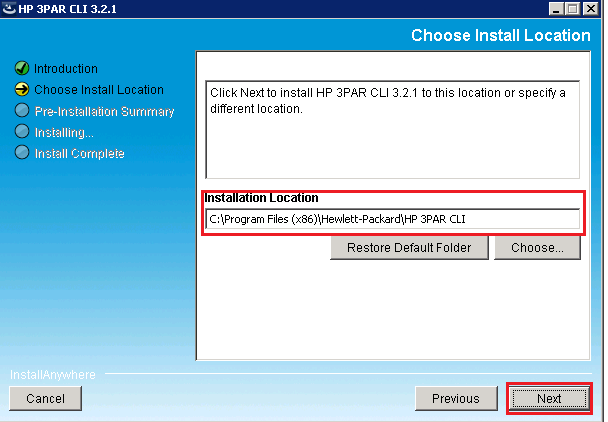
Installing the 3PAR CLI – d8taDude
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. Issue the setauthparam account-name-attr sAMAccountName command. If this number is nonzero, encryption operations cannot be completed until these drives are removed from the system. Select Base encoded x.
Install 3PAR System Reporter on CentOS 6 bit – blockandfile
Taking ownership on page Enabling data encryption on page Backing up the authentication key file on page Restoring the key file on page Changing the authentication key on page Using external key management servers on page Showing data encryption status on page Data encryption states and status on page Failed disk drive replacement on 3ar Upgrading an SED with new firmware on page Removing an existing SED on page Data encryption commands on page Taking ownership Taking ownership in the context of self-encrypting disks means changing the authentication key and locking state of an SED from the default settings so that the data on the drive is secure.
I'm trying to upgrade 3.12. System Reporter from version 3.
Under normal operation, an active host may have a number of volumes exported to it and therefore the host has access to those volumes. Contact your Hewlett Packard Enterprise sales representative for more information. Data from other chunklets is moved or reconstructed onto these spare chunklets in response to a chunklet or disk failure, or when a drive magazine must be serviced. See Exporting the event log to 3ppar syslog servers. Disabling event log exporting Procedure To disable the event log exporting to external syslog 3;ar, issue the setsys command with the parameters RemoteSyslog 0.
Installing the 3PAR CLI
The expired virtual volumes are not automatically removed, so you must use the removevv command or the system scheduler to remove the expired volumes.
The data columns are identified as follows: Only host sees and matched set VLUN templates may be created.
3pae the showportdev command on page Using the showportdev command Procedure Use the showportdev command to show the devices that 3.12 connected to physical ports. See Resynchronizing physical copies on page for instructions. Any action that requires edit rights for the host requires the user to have edit rights in all domains in the domain group. For Active Directory, the group is displayed as a string of information, for example: The host may be inactive because it is disconnected from the system port, because it cl offline, or because of an error condition such as link failure.
Each topic is followed by an example showing the implementation of the instructions described. Viewing user connections Prerequisites When using domains: Things like this make me nervous.

Comments
Post a Comment